What are API Keys and Why are they so important?
titleImagePath
date
Mar 14, 2022
slug
what-are-api-keys-and-why-are-they-so-important
status
Published
tags
System Design Basics
summary
API keys are a mechanism that allows API servers to identify client applications. This unlocks some unexpected security features
type
Post
systemType
probability
As a computer science student or software engineer, you probably have probably already come across API keys a couple of time while developing some application.
It’s this massively long encrypted string you need to send with you API request if you want to hit some APIs.
Why are API keys actually so important?
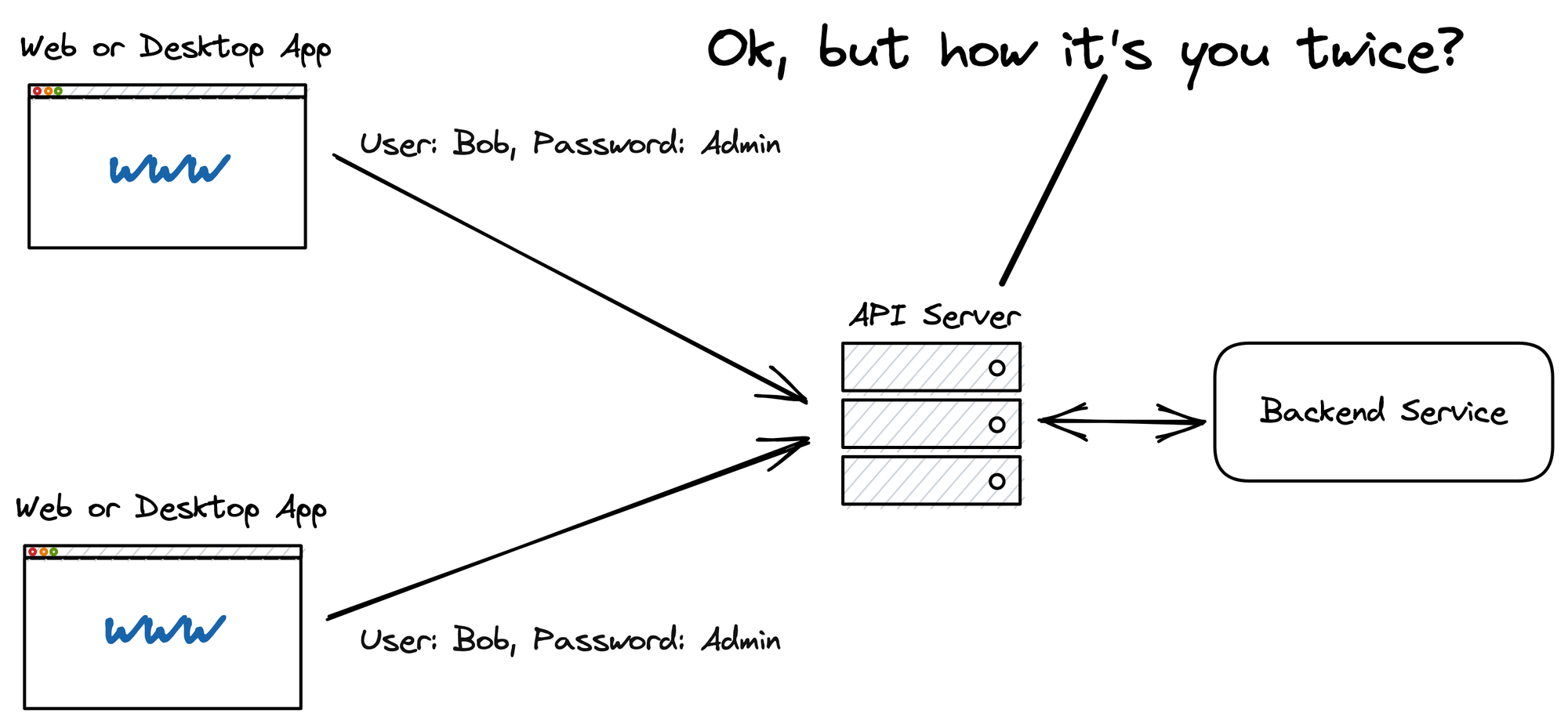
API Key authentication is a technique that was invented to overcome the weaknesses of shared credentials which was a big problem in HTTP Basic authentication. It was impossible for the server to tell apart different client applications, when multiple client use the same, valid, credentials.
In technical terms, API keys provide to things:
- Client App identification — Identify the application that’s making a call to your backends API.
- Client App authorization — Check whether the calling application has been granted access to call the API.
Let’s talk through a couple of scenarios…
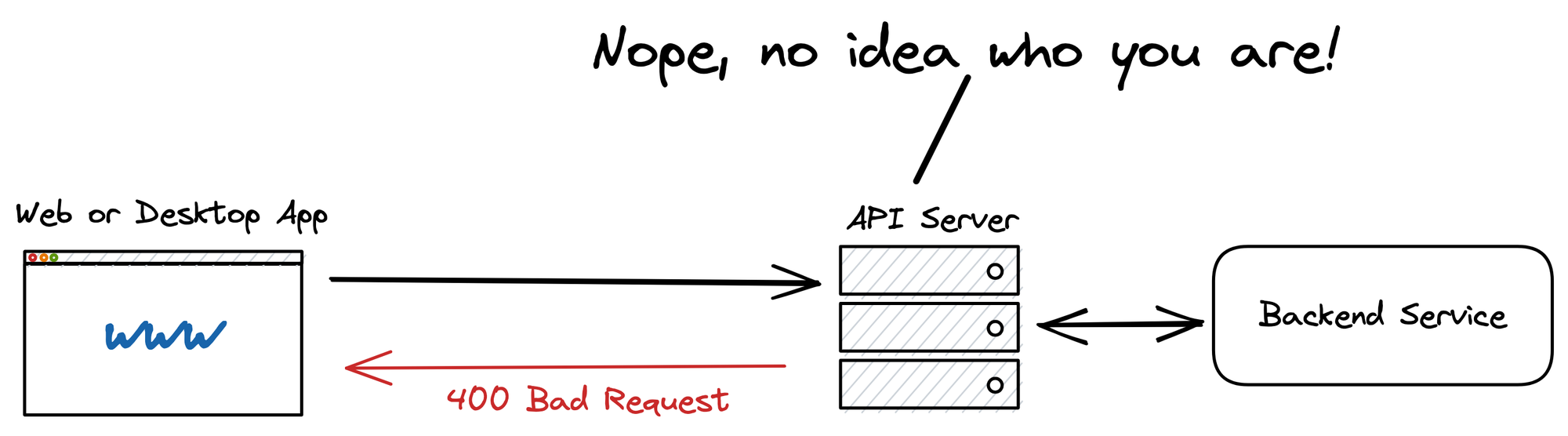
If the API key is invalid the server can simply block the access to the API.
If the API key can validated by the server, the key also acts as a unique identifier that allows to log all activity and spot and counter malicious behaviour.
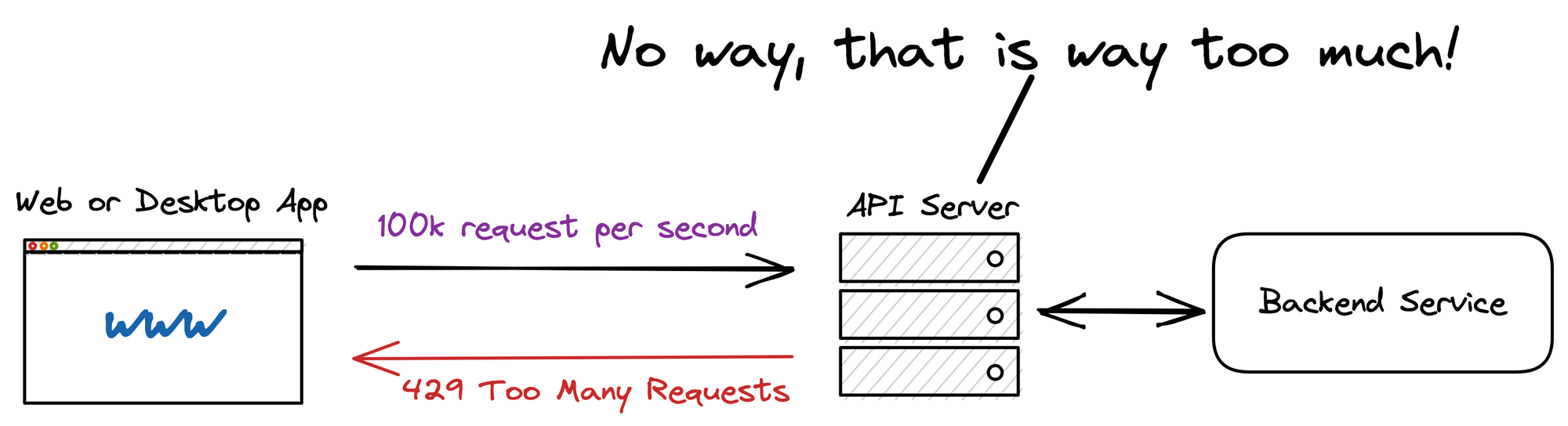
For example, API provider can set for a rate limit that restricts the allowed amount of requests per minute. Thereby api key helps you to establish a first line of defence against attempted denial-of-service- attacks.
Let’s answer some more hands-on questions.
Where to get such an API key from?
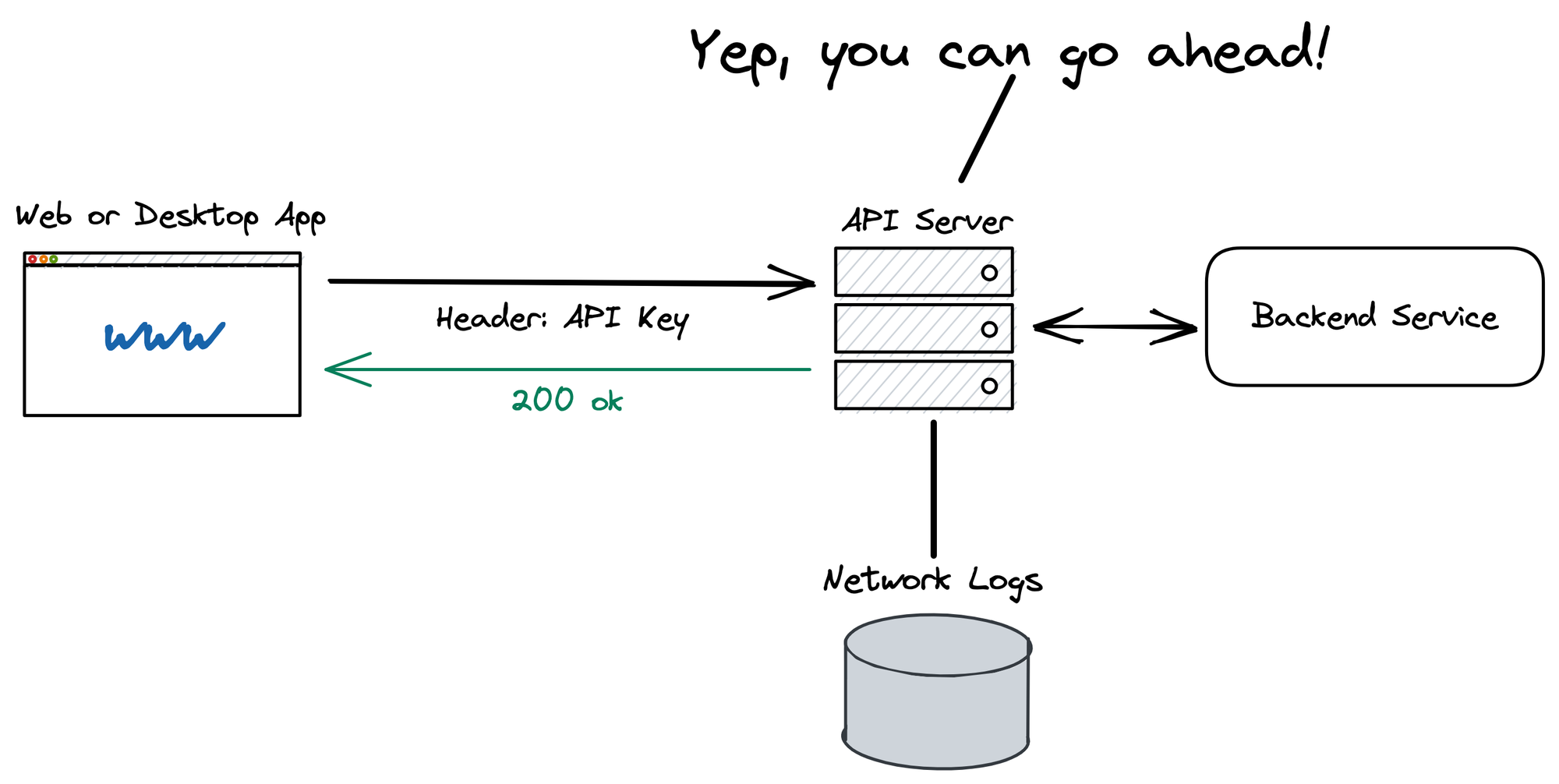
API Providers typically have a web application to manager your access to their service. That’s where you typically find a section where you can generate your API key. Then you add your API key into the header or URL of each of your requests.
And “Voila” you are able to access the API.
Two Rookie Mistakes to Avoid
If you work with API keys, there are two rookie mistakes that blow up your application security. But once you are aware of them they are easy to avoid!
1. Insecure API key storage
1. Do not embed API keys directly in code.
2. Do not store API keys in files inside your application’s source tree.
Both are very important otherwise you can be almost certain that at one point you or someone in your team will push it to github and it ends up in public eventually.
Instead of embedding your API keys in your applications, store them in environment variables!
2. API key != user authentication
Never confuse API keys for user authentication, API keys only identify applications! For user authentication they are completely useless.
- API keys can easily copy&pasted straight from the dev console or sniff from unencrypted network traffic.
- Once the key is stolen it can be used indefinitely because it has no expiration time.
- The API provider could take some counter measures to mitigate the issue but there are just more effective methods to authenticate users!